MAST Practices Covered in Mobix
Introduction
Mobix is a Mobile Application Security Testing (MAST) tool for vulnerability detection and automation of security testing of mobile applications. It detects more than 50 types of vulnerabilities. All vulnerabilities identified during the application scanning are displayed in the Mobix interface. Mobix provides information about the place of occurrence, the severity of the vulnerability, detailed recommendations for correction, and, most important, detailed recommendations for preventing similar vulnerabilities in the future.
Implementation
Mobix implements the following MAST practices:
- Byte Code Analysis (BCA) for frontend testing
- Static Application Security Testing (SAST) for frontend testing
- Interactive Application Security Testing (IAST) for frontend testing
- Dynamic Application Security Testing (DAST) for frontend testing
- Application Programming Interface Security Testing (API ST) for backend (API) testing
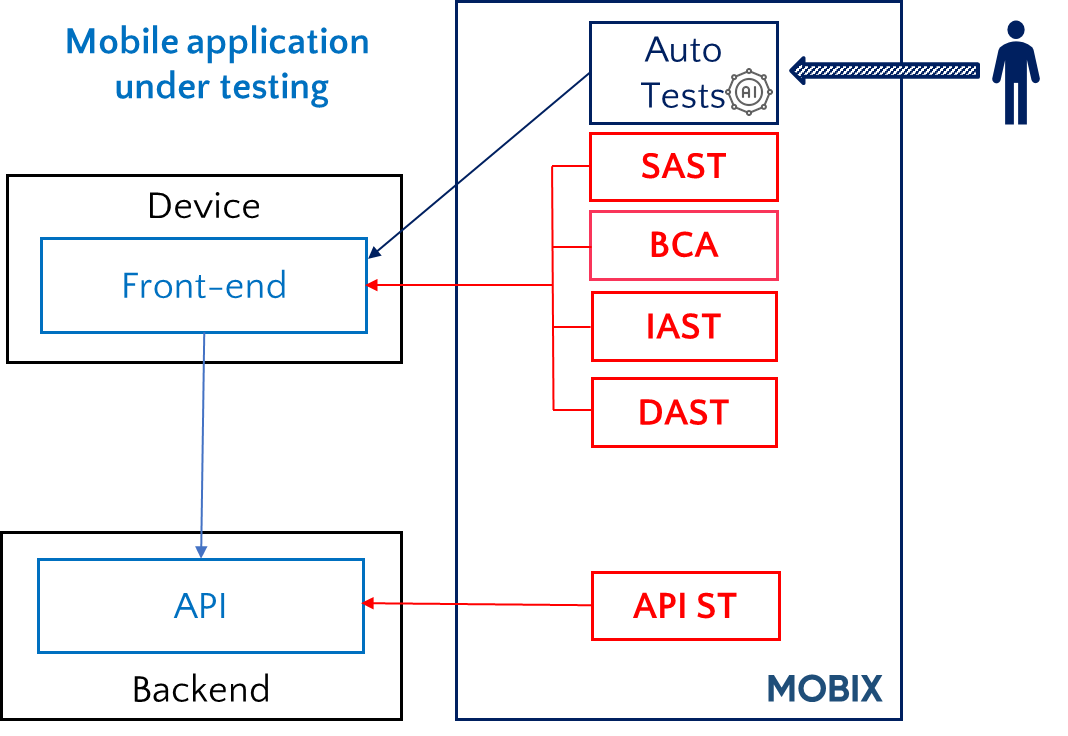
All practices realized in Mobix do not require access to the application source code. They are only applicable when a workable version of the application is available. Mobix does not support source code access-based practices. Thus, Mobix is a tool for dynamic analysis of mobile application security. It scans application security using different MAST practices, tries to simulate attacks on the application and analyzes application operation.
Not all MAST practices are implemented by Mobix in the same way. Two of them, BCA and DAST, are independent of user actions with the application under test. Mobix implements BCA and DAST practices using its security scanning ML-based model. IAST works on the basis of data collected during auto tests run. API ST is implemented based on the collection of requests/responses captured during the IAST tests run. A detailed description is provided below.
Auto tests
Mobix has a unique mechanism for recording, playback, and adaptation of auto tests. It is based on deep integration with an operating system and AI/ML (Artificial Intelligence / Machine Learning) methods. With all the complexity inside, for the Mobix user, the auto test recording looks like normal work with the application. There is no need to write test scripts or to create a special application build for testing purposes. It is enough to go through the necessary test steps in the application to perform typical business operations in the application (user login, money transfer, etc.), as if it were installed on your mobile device. Mobix just records test cases from the screen.
Mobix has a set of scan modules that performs scanning and gathers information about the application operation. One of these modules automates the collection of traffic scan during the auto tests recording and enables collection of request/response information for API ST practice.
In Mobix, the API ST practice is significantly enhanced with the request/response information collected during IAST. In general, API ST can be implemented without it, but it is much less effective at finding vulnerabilities.
BCA
As the implementation of the BCA practice, Mobix performs a static analysis of the decompiled source code. It uses the decompiled source code to analyze various application configurations that cannot be obfuscated. Mobix can determine that the application contains the wrong config from a network security point of view, or that the application is configured incorrectly and has incorrect parameters or attributes of some elements. More importantly, Mobix searches the decompiled source code and application resources for the values of sensitive information it has found through dynamic and interactive analysis, such as, a password, a token, an encryption key, and other sorts of insecure things. You can use BCA practice to ensure that the application version does not contain debug or test data and sensitive information that should not be there, and this application version is exactly what it should be.
In addition, as part of the Mobix approach to application security testing, BCA provides a solid base for implementation of the other types of “no source code access” MAST practices.
The basis for BCA is different for different mobile operating systems. Mobix performs BCA for decompiled APK files for Android and for disassembled IPA files for iOS.
SAST
BCA enables SAST for Android to be performed using decompiled source code.
Mobix implements security checks from the “classic” SAST using decompiled code. Decompiled source code is used for classical SAST operations, such as data flow analysis, taint analysis, etc. Obfuscated applications, in general, are much more difficult to analyze, but this is not so important for the SAST practice. The algorithmic part of the SAST operation does not suffer from the obfuscation of the analyzed application. The aspect of SAST that is affected by application obfuscation is the analysis of the identified vulnerabilities.
It is common in the industry to talk about SAST implementation. However, many players work with decompiled code.

IAST
IAST identifies vulnerabilities based on data collected while the application is running. Data means intercepted interaction of an application with the operating system, other applications, internal operations, file system read/write operations, etc. Mobix detects sensitive and confidential data processed by an application and verifies the security of its use by this application. It verifies that the application stores this data properly, transfers it to third-party services properly, does not store it on the device, etc.
IAST works on the basis of data collected during auto tests run or during manual application testing. The sequence of actions for recording auto tests represents typical business operations when working with an application. This enables Mobix to perform effective IAST testing.

Mobix implementation of IAST provides not only the standard functionality of this MAST practice. In addition, Mobix captures and records a collection of requests/responses during the IAST tests run. It uses this collection as input for the creation of efficient API ST tests. This input makes testing the application's API much more effective and enables more complex vulnerabilities to be found.
Mobix implements raw data collection and provision of full information about application work on the mobile device. All raw data collected can be used for further analysis or to create metrics, including the use of various tools for this purpose. For example, the network traffic is a part of the raw data collected. Mobix allows you to download network traffic in a format compatible with enterprise web application scanners (like Netsparker or Acunetix). As an additional option, this network traffic can be uploaded onto these tools for analysis.
DAST
DAST performs a set of different dynamic checks (for example, checking a weak password Keystore, data injections, unauthorized access to sensitive data, etc.). DAST considers an application as a black box and tries to find vulnerabilities using the standard mechanism for system interprocess communication. DAST attempts to attack an application in the same way as malicious applications on the mobile device that are near the application under test. Such a malicious application usually is a specifically created mobile application that can be downloaded from the Google Play store, for example. It has no special rights, works on a non-rooted device, and can attack your application through standard channels.
DAST detects different types of problems – with authentication, data injection, and so on. This allows finding a certain number of types of vulnerabilities, such as well-known ACE (Arbitrary Code Execution), RAPF (Read Arbitrary Private Files), etc.
To improve the effectiveness of DAST, Mobix uses information collected during the IAST testing. IAST test data provides information about what interface the application has, how that interface is used, and what parameters it has. Thus, you can create meaningful tests for running DAST tests and increase the testing speed and efficiency of finding vulnerabilities.

API ST
The same as in the case of DAST, Mobix implements smart API ST based on the application IAST test results. Collection of requests/responses captured during IAST allows to consider applications unlike “black box” and create additional API ST test cases to perform effective API ST. This traffic trace (request/responses sent between client and server over the network) allows Mobix to increase test coverage of API ST. In this manner, you can check, authorization, authentication, SQL injection, etc. Data collected by Mobix during IAST provides a full "application map" as input to API ST. This way, Mobix provides a mechanism for provisioning additional information about the mobile application under test.

Often the same application API is used for mobile and web versions of the application. It is often easier to run a web application to test API and capture a collection of requests/responses than to run a mobile application. Nevertheless, Mobix implements API ST for mobile applications because a web version of the application is not always available.
Summary
Mobix implements several MAST practices that offer a combination of static and dynamic analysis. Mobix also uses results of BCA testing and data collected during IAST testing as input for other types of security testing. This complex approach increases the efficiency of security testing and enables Mobix to effectively detect security vulnerabilities and ensure high quality of the security testing of mobile applications.